Describe How the Application Is Used in Wireless Security
It runs on top of UDP User Datagram Protocol and is a part of TCPIP and offers transaction support. Integrates multi-cloud environments with the on-premises network.
Everything You Need To Know About Wireless Security
It has developed at 1999.

. Many wireless communication systems and mobility aware applications are used for following purpose. As such businesses can give them to their security guards. Transmission of music news road conditions weather reports and other broadcast information are received via digital audio broadcasting DAB with 15Mbits.
Employees can also use them to communicate within the building. The following list describes the different levels of wireless security from most secure to least secure. A typical transmission path of a Wireless Communication System consists of Encoder Encryption Modulation and Multiplexing.
The wireless security protocols are WEP WPA and WPA2 serving the same purpose but being different at the same time. A request for accessing a website is sent via a WAP gateway as it provides security. What Are The Wireless Security Protocols.
The term may also refer to the protection of the wireless network itself from adversaries seeking to damage the confidentiality integrity or availability of the network. WEP Wired Equivalent Privacy is the first of Wireless Security Protocols. The most common type is Wi-Fi security which includes Wired.
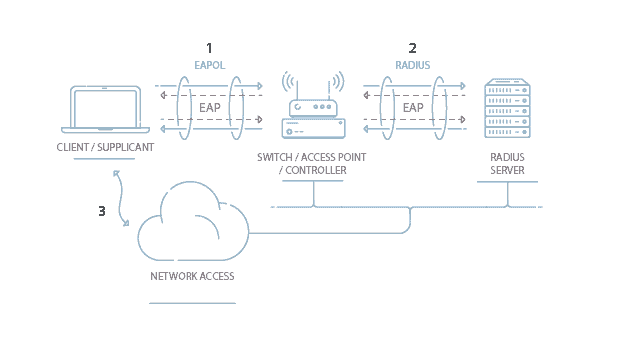
2 The authenticator asks the supplicant to verify its identity. The real security for a wireless network comes from the selection of a proven security technique. They dont suffer the same connection issues as cellphones.
Enhance Security The different types of wireless communication can enhance security. Different types of wireless security protocols were developed for home wireless networks protection. It offers data integrity privacy and authentication.
Wireless protocols also encrypt private data as it is being. Wireless networks are vulnerable in a myriad of ways some of the most likely problems being rogue access points APs and employee use of mobile devices without appropriate security precautions. The Wireless Application Protocol WAP gateway is a software system that decodes and encodes requests and responses between the smartphone micro browsers and the internet.
The server maintains the state of each authenticated user. Portal and the application will be used for all employees around the world. For example walkie-talkies transmit and receive radio signals.
Wireless protocols are designed to protect wireless networks used within homes and other types of buildings from hackers and unauthorized users. Currently the most updated and secure technique is WPA3 which was released in 2018. Even if the wireless network security is compromised the hacker is not able to view the content of the trafficpacket in transit.
Technology for radio wireless local area networks Quality audio technology Q5. Applications of wireless communication involve security systems television remote control Wi-Fi Cell phones wireless power transfer computer interface devices and various wireless communication-based projects. LEAP is a good choice.
Wireless LANs or WLANs offer many advantages over. Identify the correct description for IaaS. For personal communication a universal mobile telecommunications system UMTS phone might be.
The Transmission Path. This layer contains Wireless Transaction Layer Security WTLS. Typically wireless network security is delivered through wireless devices usually a wireless routerswitch that encrypts and secures all wireless communication by default.
Follow these wireless network security best practices to ensure your companys WLAN remains protected against the top threats and vulnerabilities. Instead Wi-Fi has become the go-to network access technology for users and endpoints. This standard provides two different modes of operation.
List the steps for RADIUS authentication with a wireless device in an IEEE 8021x network. WiFi security algorithms have been through many changes and upgrades since the 1990s to become more secure and effective. At the beginning maximum 64-bit encryption was allowed in US.
So WEP was using 64-bit encryption. 10Base-T RFC 826 IEEE 80211 ISO 5750 NSE 2 Cloud Security Q1. It was developed to protect the wireless data between Clients and Access Points APs towards hackers.
Which of the following would BEST describe this authentication process. Also called EAP-Cisco LEAP is a wireless security protocol created by Cisco to address the weaknesses in WEP and WPA. This layer contains Wireless Datagram Protocol.
3 The supplicant sends identity information to. Both ends of every link must use the same encryption standard. 1 The device requests from the authenticator permissions to join the network.
Moreover wireless intrusion detection and prevention systems also. Wireless security is the prevention of unauthorized access or damage to computers or data using wireless networks which include Wi-Fi networks. Lightweight Extensible Authentication Protocol LEAP.
For many businesses wired Ethernet is no longer supreme. The development team has designed the application to use token-based authentication when users login. As previously mentioned there are four wireless security protocols each varying in strength and ability.
Wi-Fi is based on which standard. The signal from the source is passed through a Source Encoder which converts the signal in to a suitable form for applying signal processing techniques.

What Is Open System Authentication Osa

No comments for "Describe How the Application Is Used in Wireless Security"
Post a Comment